WordPress admin email addresses are among the most targeted aspects of a website. As WordPress powers over 40% of websites globally, this immense popularity makes it a prime target for hackers seeking to exploit vulnerabilities. Admin email addresses, often linked to critical login details and recovery channels, are highly valuable to cybercriminals. These email addresses may even grant full access to a WordPress site, putting sensitive data at risk.
Hackers target admin email addresses because they provide unauthorised access to WordPress sites. These email addresses allow hackers to manipulate site settings, reset passwords, and steal valuable information. Understanding how hackers mine these email addresses and knowing how to secure your site are essential steps in maintaining security. In this article, we will examine the methods hackers employ and provide practical steps to safeguard your WordPress site against these attacks.
Why Are WordPress Admin Email Addresses Targeted?
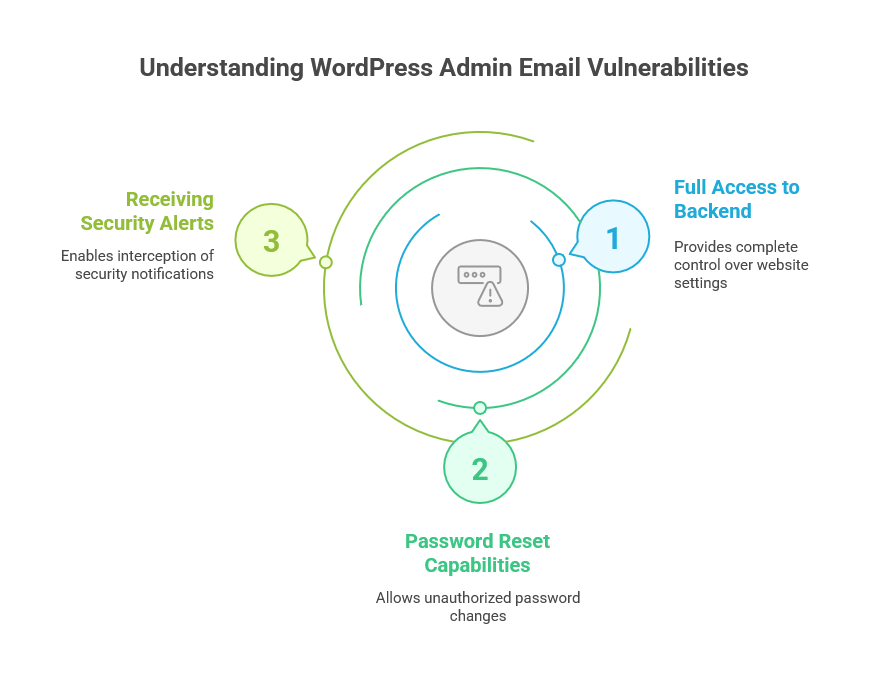
Admin email addresses serve as the core of a website’s management system. Site owners use them for password recovery, important notifications, and managing user roles. Since this email is usually tied to the admin account, hackers see it as the “key” to accessing critical site features, including:
-
Full access to the WordPress backend: Admin emails are often linked to the highest level of access on a WordPress website.
-
Password reset capabilities: If a hacker gains control of the admin email, they can easily request a password reset and lock the rightful owner out of their account.
-
Receiving security alerts: The admin email address is often a prime target for hackers seeking to bypass security notifications.
Admin email addresses contain vital information that can make a WordPress site more vulnerable to unauthorised access. Hence, it is crucial to understand how hackers attempt to access them.
How Do Hackers Mine WordPress for Admin Email Addresses?
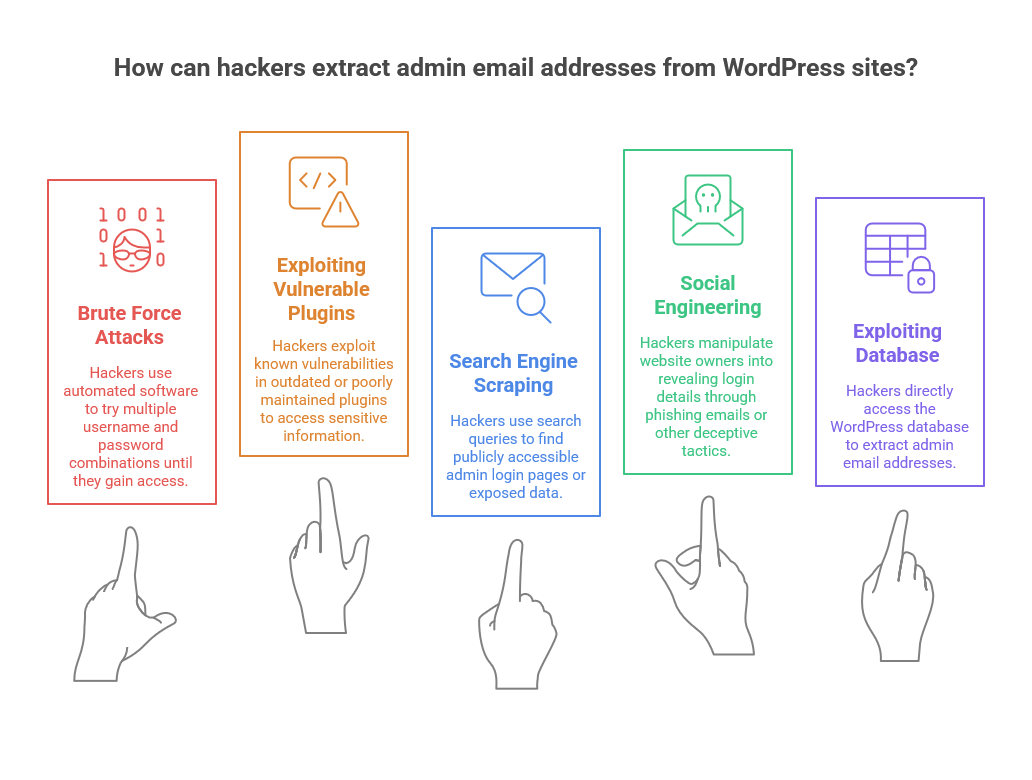
Hackers employ several strategies to extract admin email addresses from WordPress websites. Some of the most common techniques include brute-force attacks, exploiting vulnerable plugins, social engineering, and scraping publicly available data. Let’s take a closer look at each method:
a. Brute Force Attacks
A brute-force attack occurs when a hacker uses automated software to try multiple combinations of usernames and passwords until they gain access to an account. WordPress sites, especially those with weak passwords or default usernames like “admin,” are prime targets for brute-force attacks. Once hackers succeed, they often gain access to sensitive information, including the admin email address associated with the account.
Hackers use powerful tools to automate this process, which significantly increases their chances of finding the correct login credentials. Some WordPress sites make it even easier for hackers by using common username and password combinations.
b. Exploiting Vulnerable Plugins and Themes
WordPress plugins and themes are one of the main reasons why WordPress is so customizable, but they also open doors for hackers. Many WordPress site owners use plugins that have known vulnerabilities. Hackers can exploit these vulnerabilities to access your WordPress website and extract sensitive information such as admin email addresses.
For instance, an outdated plugin or theme can be an entry point for hackers. If the plugin has a known flaw, hackers can use tools to scan for sites running this vulnerable software and exploit the weakness to gain access.
c. Search Engine Scraping
Search engine scraping is another common method that hackers use to gather admin email addresses from WordPress sites. Hackers use specific search queries to find WordPress websites with publicly accessible admin login pages or other exposed data. By reviewing search engine results, hackers can identify email addresses associated with administrative accounts.
This is one of the easiest ways hackers can gather admin emails, as it doesn’t require technical skills or malicious intent—just the use of Google search operators or similar tools to find WordPress sites with exposed information.
d. Social Engineering and Phishing
Social engineering is one of the most dangerous methods used by hackers to gain access to WordPress admin emails. In this method, hackers attempt to manipulate website owners into revealing their login details, including admin email addresses.
A common social engineering tactic is phishing emails. These emails often appear to originate from legitimate sources, such as WordPress, plugin developers, or hosting providers. The emails may contain messages urging website owners to click on links or provide sensitive information. If the victim clicks on a malicious link or provides login credentials, the hacker gains access to the admin account and email address.
e. Exploiting the WordPress Database
In some cases, hackers can directly access the WordPress database to extract the admin email address. This happens if the database isn’t securely configured or if hackers can exploit a vulnerability to gain access.
WordPress stores critical information, including user accounts and email addresses, in its database. Hackers can extract this data once they gain access, making it crucial for WordPress site owners to secure their database with strong passwords, encryption, and firewalls.
What Happens When Your Admin Email Gets Compromised?
If a hacker successfully gains access to your WordPress admin email, they can potentially take over your website. Here are some of the consequences:
-
Full Control Over Your Website: With access to the admin email, hackers can reset the login credentials for your website, locking you out.
-
Theft of Sensitive Information: Hackers can use the admin email to access user data, transaction information, or any other sensitive data stored on your WordPress site.
-
SEO Damage: A compromised website may be used to send spam or host malicious content. Search engines like Google may flag your website, which can harm your SEO rankings.
-
Reputation Damage: A hacked website damages your reputation, leading to a loss of trust from users or customers.
How to Protect Your WordPress Admin Email from Hackers
To prevent hackers from mining your WordPress admin email, it’s essential to implement strong security practices. Here are some of the best ways to secure your website and protect your admin email address:
a. Use Strong Passwords and Two-Factor Authentication
The simplest and most effective method to protect your admin account is by using a strong password. Avoid using common words or easy-to-guess combinations. Use a mix of upper and lower-case letters, numbers, and special characters.
In addition to strong passwords, enable two-factor authentication (2FA) on your WordPress site. This adds an extra layer of protection by requiring a second form of identification (such as a code sent to your phone) before logging in.
b. Keep WordPress, Plugins, and Themes Updated
One of the most crucial steps in securing your WordPress site is to ensure it is always up to date. WordPress frequently releases updates to patch security vulnerabilities, so ensure that you install these updates as soon as they become available. This also applies to plugins and themes. Vulnerable plugins and themes are prime targets for hackers, so updating them regularly is crucial.
c. Limit Login Attempts
Brute-force attacks rely on multiple login attempts to guess the correct password. To mitigate this risk, limit the number of failed login attempts on your website. Several security plugins, such as Wordfence or Limit Login Attempts, allow you to configure this feature and lock out users after a certain number of failed attempts.
d. Use Security Plugins
WordPress security plugins provide an extra layer of defence. Plugins like Wordfence Security, iThemes Security, and Sucuri Security can help protect your website by adding firewalls, scanning for malware, and blocking malicious login attempts.
e. Backup Your Website Regularly
Regular backups are essential for any WordPress site.If hackers compromise your website, you can restore it to a previous, secure version. Many plugins allow you to automate regular backups, ensuring your data stays protected.
f. Use HTTPS for Encryption
HTTPS encrypts the connection between your browser and the website, securing any data exchanged, including admin login credentials. Ensure your WordPress site uses HTTPS to prevent hackers from intercepting your admin email and other sensitive data.
FAQs
-
What is the easiest way hackers target WordPress admin email addresses?
Hackers often use brute force attacks and search engine scraping to find exposed admin email addresses. -
Can hackers access my WordPress admin email through a vulnerable plugin?
Yes, outdated WordPress plugins or themes with security flaws allow hackers to exploit them and gain access to sensitive data. -
How can I tell if my WordPress admin email is exposed?
Regularly audit your site and check for exposed login pages or accessible admin email addresses. -
What should I do if my WordPress admin email gets hacked?
Immediately change your password, enable two-factor authentication, and review your website for any unauthorised changes. -
Do I need a backup plan to protect my admin email?
Yes, regular backups allow you to restore your site to a safe version if it is compromised.
Hackers continually target WordPress websites for vulnerabilities, and admin email addresses are a high-value target. Once hackers gain access, they can easily take control of your site, steal sensitive data, and harm your reputation. By using strong passwords, enabling two-factor authentication, regularly updating your WordPress site, and implementing security plugins, you can significantly reduce the risk of email mining and protect your WordPress site from malicious attacks. Stay proactive and safeguard your website today.

